Get-rich schemes existed before the Internet, but people only received them by mail. Nowadays, these have become crypto scams that pollute the ocean of information.
People looking to improve their financial situation fall prey to websites promising unprecedented wealth. Worse, they masquerade as reputable websites like the Inquirer.
READ: How to avoid QR code scams
However, the nonprofit digital forensics foundation Qurium exposed one of these crypto scams. It revealed a fraudulent network that spans multiple websites and countries.
How do these crypto scams work?
It is important to understand how crypto schemes function before diving into a specific one. Qurium says these scams operate in websites “designed by ‘Affiliates’ to drive traffic (leads) to the ‘Advertisers.”
Advertisers extract personal data from the victims to convince them to invest in nonexistent products and services. “Affiliate Networks” pay affiliates to promote their financial products.
Moreover, they run traffic management software that tracks affiliates’ performance and actions taken by victims.
For example, affiliates earn rewards and a fee commission when a victim enters a third-party office.
The latter is otherwise known as a “boiler room.” As a result, the system ensures everyone earns income from the scheme.
How did Qurium discover the crypto scheme?
Qurium explained it spots traffic management software solutions to root out bogus financial investments. As explained earlier, these scams rely on them to track affiliate performance.
These tracking programs only share with affiliates and publishers instead of the public domain. Consequently, tracing their benefactors can be relatively straightforward.
The digital forensics foundation said it worked with French news outlet Le Monde to identify the Russian Affiliate network RPT linked to crypto scams.
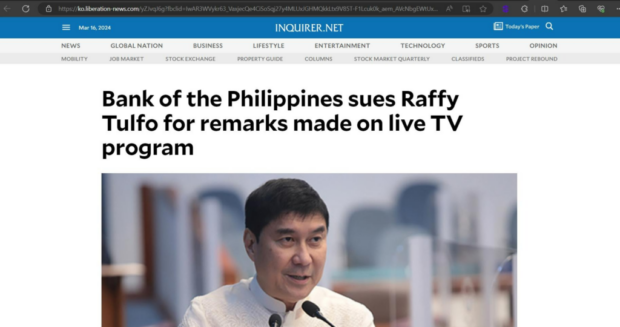
Its recent investigation started with the impersonation of the Philippine Daily Inquirer, as observed by Internews’ online monitoring on disinformation and influence operations.
It examined an article promoting a crypto investment and impersonated Raffy Tulfo, a Filipino politician and media personality.
Fake articles from the Inquirer and the publishing platform Medium featured the senator. Specifically, the promoted site was a clone of the real Inquirer.net content but used a different domain, liberation-news(.)com.
This article puts periods in parentheses to ensure readers do not accidentally open these websites.
These articles provide a link to the domain name snbghllytrk(.)com. Then, it redirects people again to domains under the IP address 162.19.231(.)202:
- official-platform{.}com.
- official-site-offer{.}com.
- official-site-platform{.}com.
- the-official-website{.}net.
- best-money-deal-daily{.}com.
The same machine includes these other domains:
- devself{.}xyz.
- newsbbi{.}com.
- immediate-1x-cipro{.}online.
- Immediate-neupro-2-0{.}online.
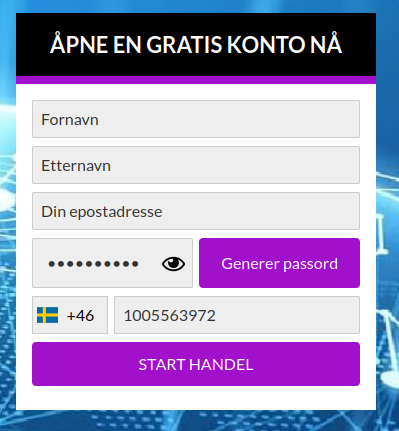
Also, the websites that promote crypto scams display this form:
Qurium reveals the crypto scams’ affiliate networks
The Qurium investigation’s main goal is to attribute the crypto scams to three affiliate companies based in Tel Aviv. Many sources have been describing these schemes, but they have not pinpointed those who profit from them.
Eventually, the foundation’s investigation revealed the deeper workings of the crypto scheme system.
The scams had different names, but they used the domain name snbghllytrk(.)com as their entry point.
A quick search for snbghllytrk revealed that Qurium was not the only organization investigating the issue.
Qurium stated Sam Harper from Cyber Citoyen (Quebec) and Stéphanie Blanchet Nameshield CTI Laboratory (France) were following the same leads.
READ: How to make money on X
Both looked at activities related to snbghllytrk(.)com in different periods. Surprisingly, they found the data collection form sent information to different locations:
- TrafficON
- Supreme Media
- Getlinked and ROI Collective
Affiliate network #1: TrafficON
Since March 2024, Nameshield Lab has been investigating misleading social media ads. They spoof French celebrity names and major news media to promote crypto scams.
The cybersecurity company traced 400 Medium publications. Eventually, it identified a specific pattern passing through three different domain names to open the sales page:
TrafficOn hosted one of the most prolific crypto affiliates. It is an affiliate network active since 2014, which specializes in online betting, gambling, and trading.
It operates an earnings-per-click (EPC) or commission (CPA) program with a minimum payment of $100. Moreover, it boasts of being in a “group that has paid more than 50 million dollars per year to Affiliates and Partners.”
This “group” is Affiliomania Ltd, which has a headquarters in Ramat Gan, Tel Aviv. Also, it owns Proftit, a subsidiary that develops a CRM for complete business automation solutions for Finance and Gaming.
Affiliomania gained notoriety for illicit activities. In 2018, its name surfaced when authorities uncovered a binary options fraud.
The company had a connection with BoaElite, allegedly “the largest affiliate network for the financial markets.”
SpotOption Ltd launched BoaElite in 2013. The former is a Ramat Gan-based binary options platform provider founded in 2009.
Hundreds of websites used it in a massive global scam. Qurium says it is unclear what happened to BoaElite.
However, Qurium says there are hints that it resurrected in TrafficOn. Affilomania hides its connection with TrafficOn, but ZoomInfo lists most TrafficOn employees under Affilomania.
Affilomania sustains its network with its “Candy Shop.” It pays affiliates with “TraffiCoins” for every lead turned into a sale.
These digital credits allow them to “purchase” high-end products like iPhones and Rolex watches, which have market values that exceed €100,000.
Qurium discovered a form responsible for forwarding victim data. It uses a WordPress plugin named suprememedia-api.
The plugin called the Javascript function js/ip.js to geolocate readers. It identifies locations by requesting the online service ipinfo(.).io.
Once the website learns the user’s country from IPInfo, it shifts the form and content of the form to the victim’s language.
The victim provides personal information, and then the form sends the data to ss2701api(.)com via an API.
The acronym stands for “application programming interface,” which is software that lets two apps communicate with each other.
Qurium used the online tool urlscan(.)io to find sites using the suprememedia.api plugin:

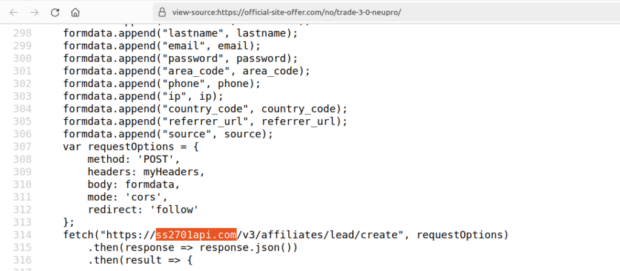
Analyzing the source code of the contact form reveals that the domain name ss2701api(.)com fetches content displayed to victims.
READ: 10 ways to make money with ChatGPT
Qurium says these findings link the domain name ss2701api(.)com to the WordPress plugin suprememedia-api.
Affiliate network #3: ROI Collective
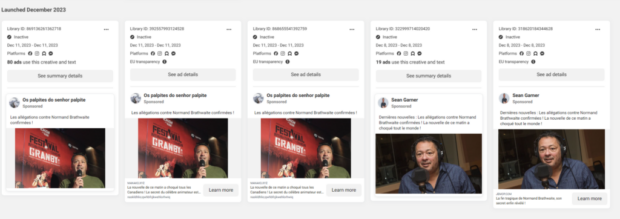
In March 2024, Cyber Citoyen discovered Adds featuring Canadian TV personality Normand Brathwaite. They promoted crypto investments on Facebook.
Nowadays, new Adds appear on the social network featuring other local celebrities. Some redirect users to fake sites that masquerade as reputable news sources like the Journal de Montréal or La Presse.
Qurium researched Adds that pointed to various Medium articles a secret financial investment app. These “articles” say the celebrity got into trouble for sharing the link to it.
Of course, this scenario never happened. Their final landing page included a different code for sending victim data to an affiliate network.
Qurium used urlscan(.)io to download and analyze different versions of this API code. As a result, they extracted the various “endpoints’ used by the software:
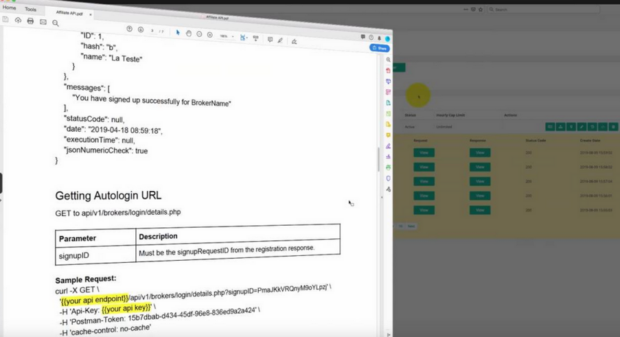
Qurium discovered recently used domain names like server.fl-bckup(.)com, server.fsbckup(.)com, and server.flbckup(.)com.
They weren’t useful because they had confidential registration info. However, the foundation learned the endpoint of this API used in boiler-room type scams had the following domains: server.getlinked(.)io and server.roicollective(.)com.
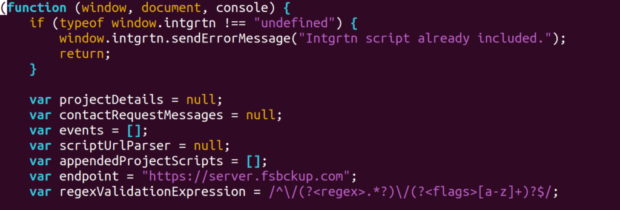
Getlinked and ROI collective
Getlinked is a software platform for managing affiliate marketing campaigns. Qurium contacted Getlinked and a spokesperson said:
“Getlinked is a software (SaaS solution) used by many companies around the world to manage their affiliate networks, online traffic, leads, campaigns, and affiliates.”
“Our terms of service strictly prohibit any illegal activity including copyright infringement, etc. [If we] think anyone breached our terms, it is done without the knowledge, consent, or permission from our side, and you should approach them directly.”
“All the affiliate relationships are between them and the affiliate networks, and we have no knowledge or take part in it.”
Qurium checked this claim by searching a video-hosting platform, vidit(.)io, from the Bulgaria-based company Perspecta Ltd.
Searching this domain on urlscan(.)io returns results associated with the same API related to Getlinked and ROI Collective.
ROI Collective is an affiliate marketing network specializing in online gambling. Its parent company, Blue Media, is in Hong Kong.
An interview on Facebook shows Matt Aizen, ROI Collective affiliate manager, saying his company can see the activities of its affiliates.
“We supervise the traffic from the click all the way to the deposit, all the way to the sales themselves.”
Qurium reached out to the ROI collective but has not received a response at the time of writing.
Bulletproof infrastructure
Qurium found the crypto scams connected to bulletproof infrastructure spread worldwide. Cybersecurity firm Netscout defines bulletproof hosting or infrastructure as:
“A technical infrastructure service provided by an internet hosting service that is resilient to complaints of illicit activities, which serves criminal actors as a basic building block for streamlining various cyberattacks.”
Searching for other websites that used the API call “api/v1/brokers/login/ revealed online postings related to scams coinnewsspan(.)com and profit-edge(.)online.
It also found different domains used to run financial scams. Also, Alliance64 (Russia), Snel (Netherlands), 3NT SOLUTIONS (Russia), BlackHost (Seychelles), and IPConnect (Seychelles) host them:
- 80.87.206.180 Alliance64 (RU)
- 193.34.166.202 Snel (NL)
- 185.162.235.87 Alliance64 (RU)
- 38.180.33.13 3NT SOLUTIONS LLP (RU)
- 185.142.236.235 Black.HOST (SC)
Qurium says Black.host is a bulletproof hosting provider registered in the Seychelles and an address in Switzerland.
Conclusion
This research reveals a large affiliate marketing network that promotes crypto scams. Qurium, Cyber Citoyen, and Nameshield Lab identified three affiliate networks using this scheme.
Their findings revealed the affiliate companies behind these schemes: Tel Aviv-based TrafficON, Supreme Media, Getlinked, and Hong Kong-based ROI Collective.
They dealt with various forms of financial fraud like binary options and Forex investments evolved into the promotion of crypto scams.
Revealing these entities is a crucial step in stopping these scams, protecting future victims, and keeping the Internet safe.
Credit: Source link